Alkaid 01
Alkaid 01 is a system designed for a cybersecurity exercise. In this project, I cooperated with Gronext as the team lead of design. It was my first time designing a system with such complexity, which was quite challenging and fun at the same time.
Role
UI/UX design,
2D Animation
Client
Gronext
Year
2025

1
UX
- TA Interview
- Flow
- Wireframe
2
UI
- Software
- Website
- Editor
3
Animation
- Attack
- Defense
Alkaid 01,
a powerful tool for hosting cybersecurity exercise
Summary
Alkaid 01 is a service that allows people to host a CTF event. We have different interfaces for various users and provide real-time animated displays on a big screen for guests to understand the overview of the competition.


Interview
I interviewed the people who participated in cybersecurity exercises as different characters. As a result, I found that there are six types of users, which can be categorized in two ways:
-
Before the exercise
-
Host
-
Admin
-
Project manager
-
Problem Setter
-
-
-
During the exercise
-
Competitor
-
Attack team
-
Defense team
-
-
Judge
-
Guest
-

Goal
-
The host can set up the environment of cyber security exercise on a website.
-
Problem Setters can design challenges through editor software.
-
Both teams can complete all their task on a website.
- Building a chat allows people to do the following actions:
- The host can announce some information in public chat.
- Each team can discuss within private chat.
- Create a collaborative markdown workspace.
- Guests can understand the competition through display screens without background knowledge and feeling bored.

Flow

The host
The admin has the highest authority in the system. They assign a project manager to hold an event.
As for the project manager(PM), Project managers need to make sure everything works in the exercise. They need to set the rules of the exercise, assign different roles to people, manage the information in public chat, and communicate in time.
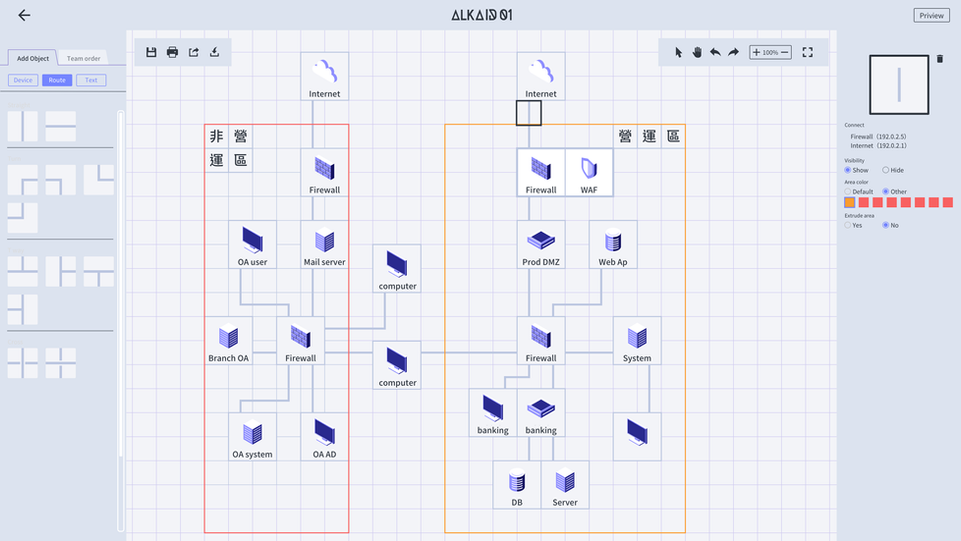
Problem Setters use our editor to design the topology of services and embed vulnerabilities within devices for both teams to find.

Attack Team
The attack team will score if they find vulnerabilities in the defense team's service and the flag hidden inside.

Defense Team
They need to maintain the service provided by the host while searching for cybersecurity vulnerabilities and attempting to fix them. If a hacking attack occurs, the defense team must investigate and write a report on the attacker.

Judge
The judges need to evaluate every defense report and award points while ensuring both teams follow the rules.

Guest
Most of them are from the government and have little background knowledge of cybersecurity. Therefore, I need to visualize the events during the exercise to provide them with an overview of the situation.
Display Screens
Display screens allow docents to explain the overview of the competition to guests at the venue.

Topology and Team Overview (upper left), Team Score Trend Chart (upper right),
Team Ranking (lower left), Status of Defensive Team Devices (lower right).
Animation
The animations of the Topology and Team Overview will be triggered in the following situations:
-
Attack team
-
Attack animation will be triggered when attack team send the right flag.
-
Title
-
First blood
-
Score
-
-
-
Defense team
-
Defense animation will be triggered when attack team send the wrong flag.
-
Title
-
Defended
-
-

Feedback
Alkaid01 has been used by multiple government agencies. The following are their feedback:
-
The interfaces are beautiful and easy to understand.
-
The editor is convenient.
-
The animation makes the competition more exciting.